It's been way too long since we published a blogpost, but our product management and R&D team has been quite busy over the past year. Our main focus has been around hardening the analysis engine, supporting additional threat types (e.g. our newly added URL analysis capability), growing the community and building an enterprise grade product. In this short blogpost, we will start out our blog revival and showcase a few capabilities of the admin panel / backend. Something most users have not seen yet, as it is only available to admins. Duh. ;)
Accessing the admin panel
When logged in to the webservice as an admin (note: the initial admin is the first user that is setup when deploying a vanilla system), the user menu at the top right will be populated with an "Admin panel" menu item:
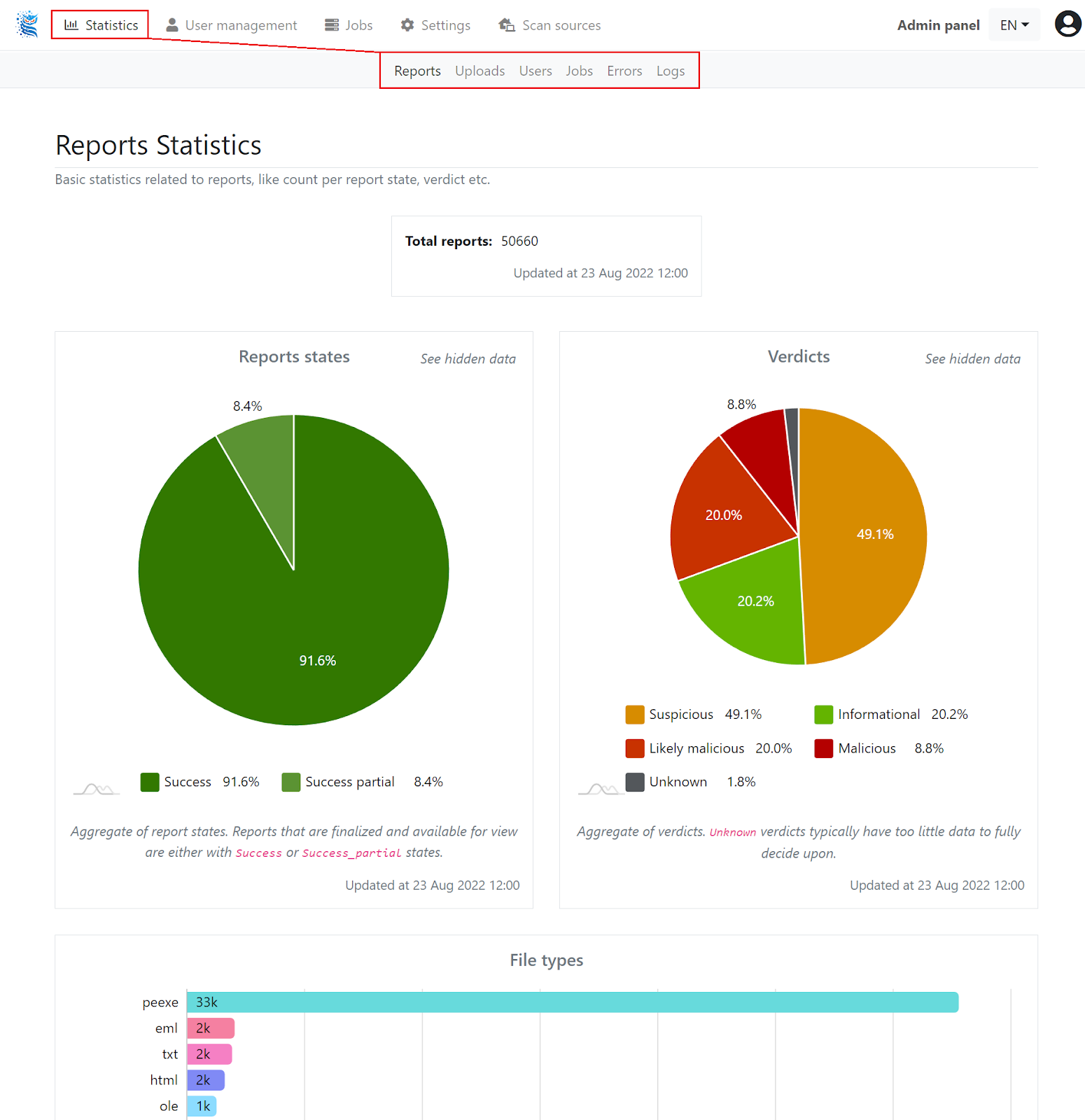
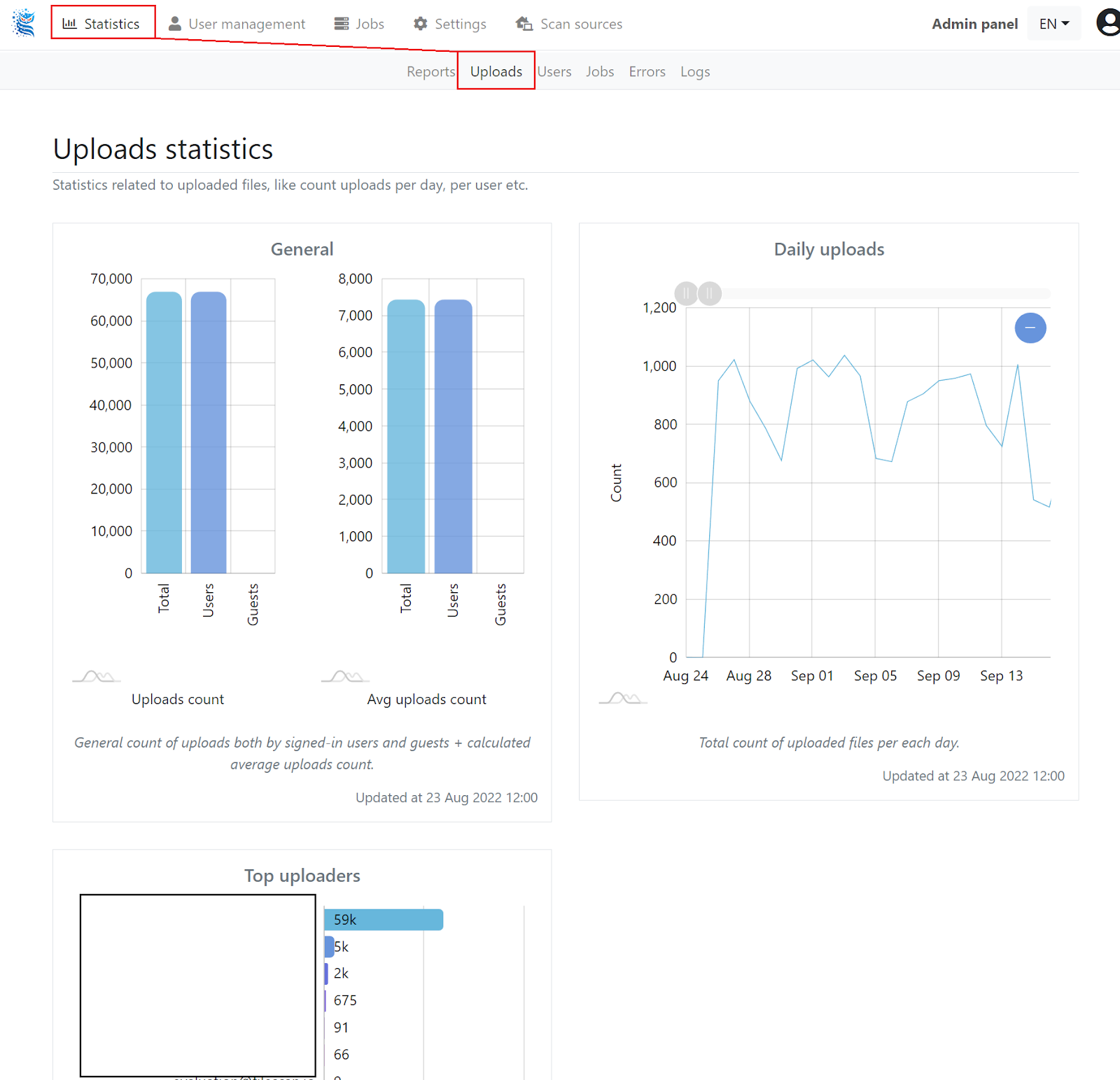
The landing page of the admin panel is the "Statistics" sub-page (see top menu) and will look similar to this:
User Management
The individual group permissions (i.e. which group is allowed to access which feature) are configurable at the Settings - Feature Access subpage:
Note: as by default every user is part of the "User" group, the "Intel" user will be able to access both basic "Threat intelligence" and "Advanced intelligence" features.
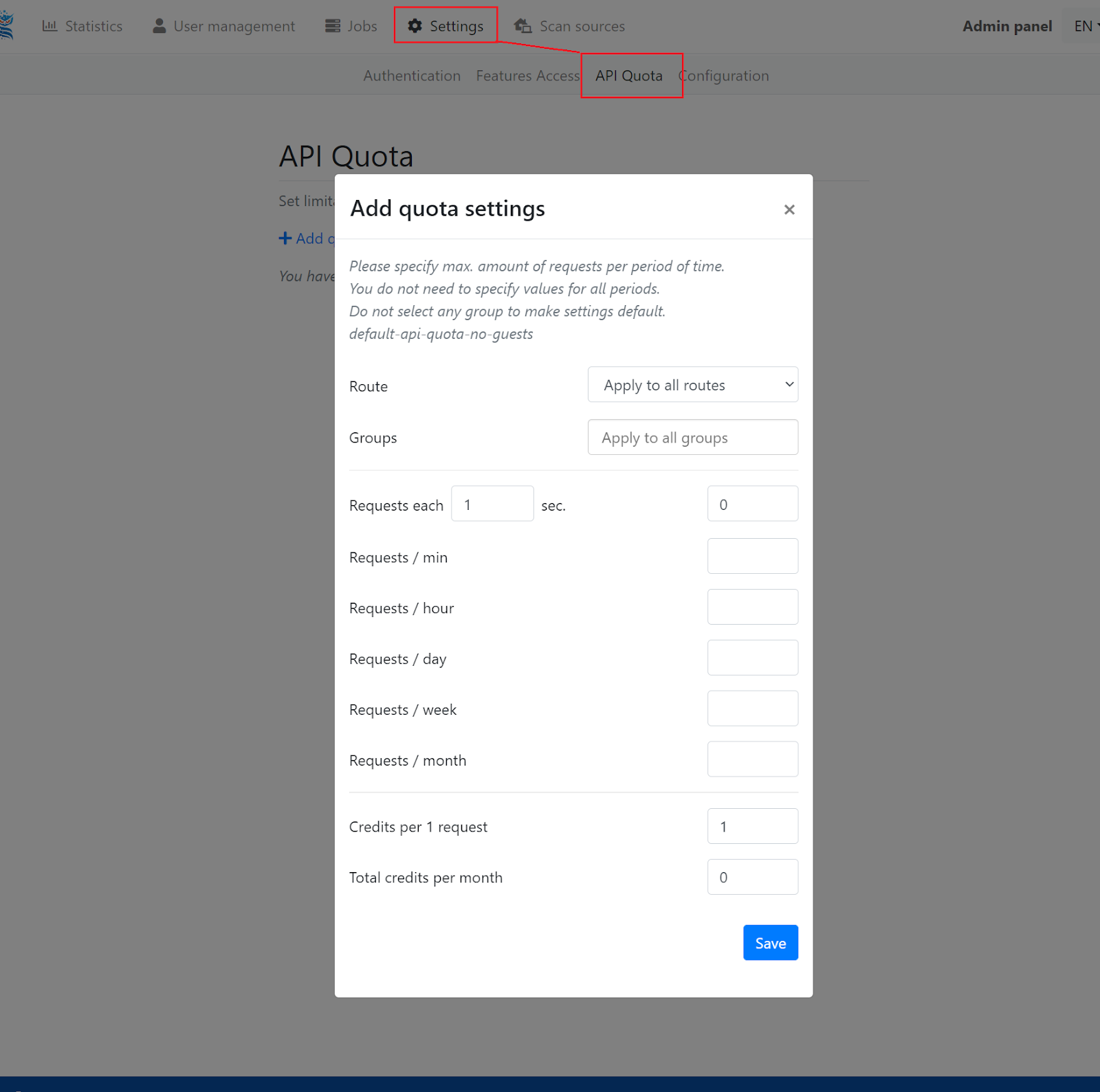
API Quotas
OAuth 2.0
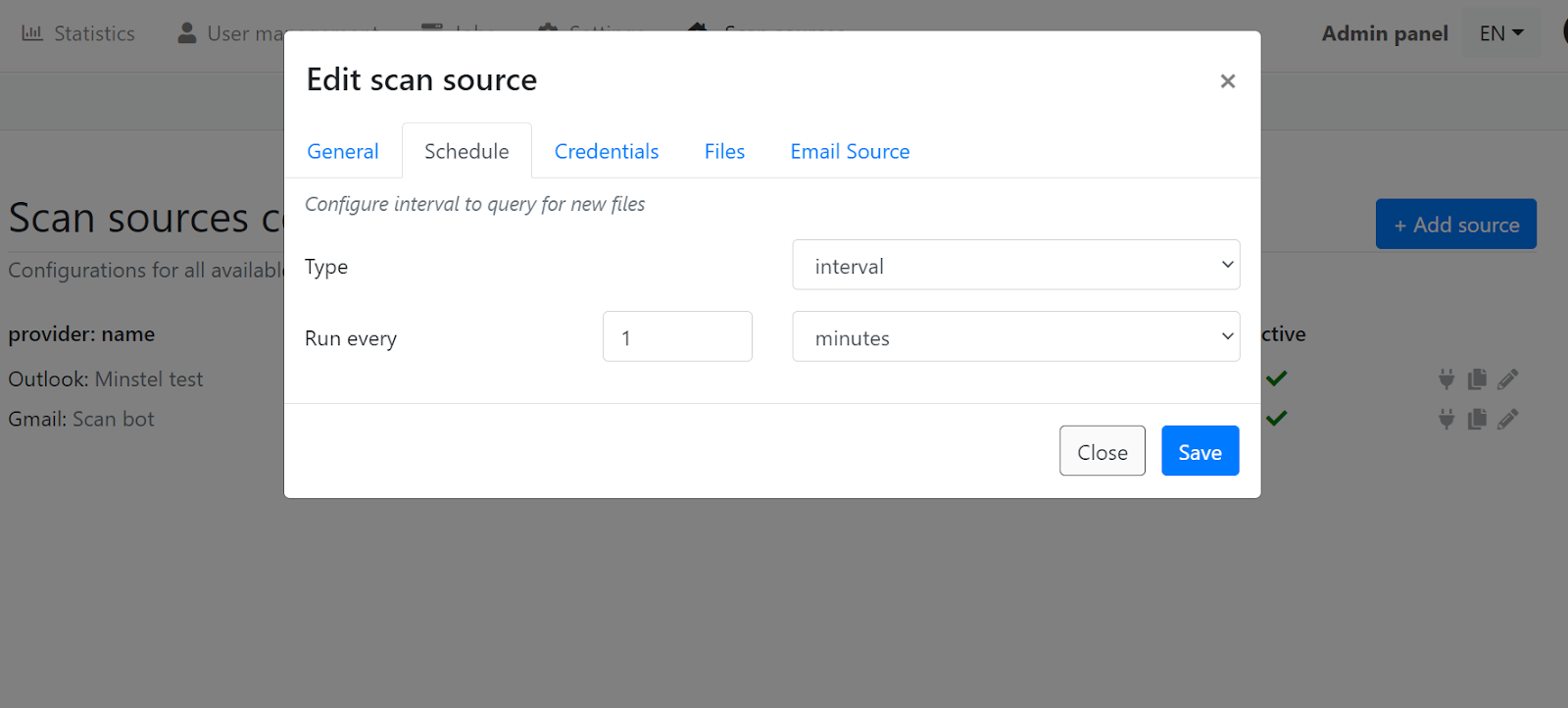
Scan Sources
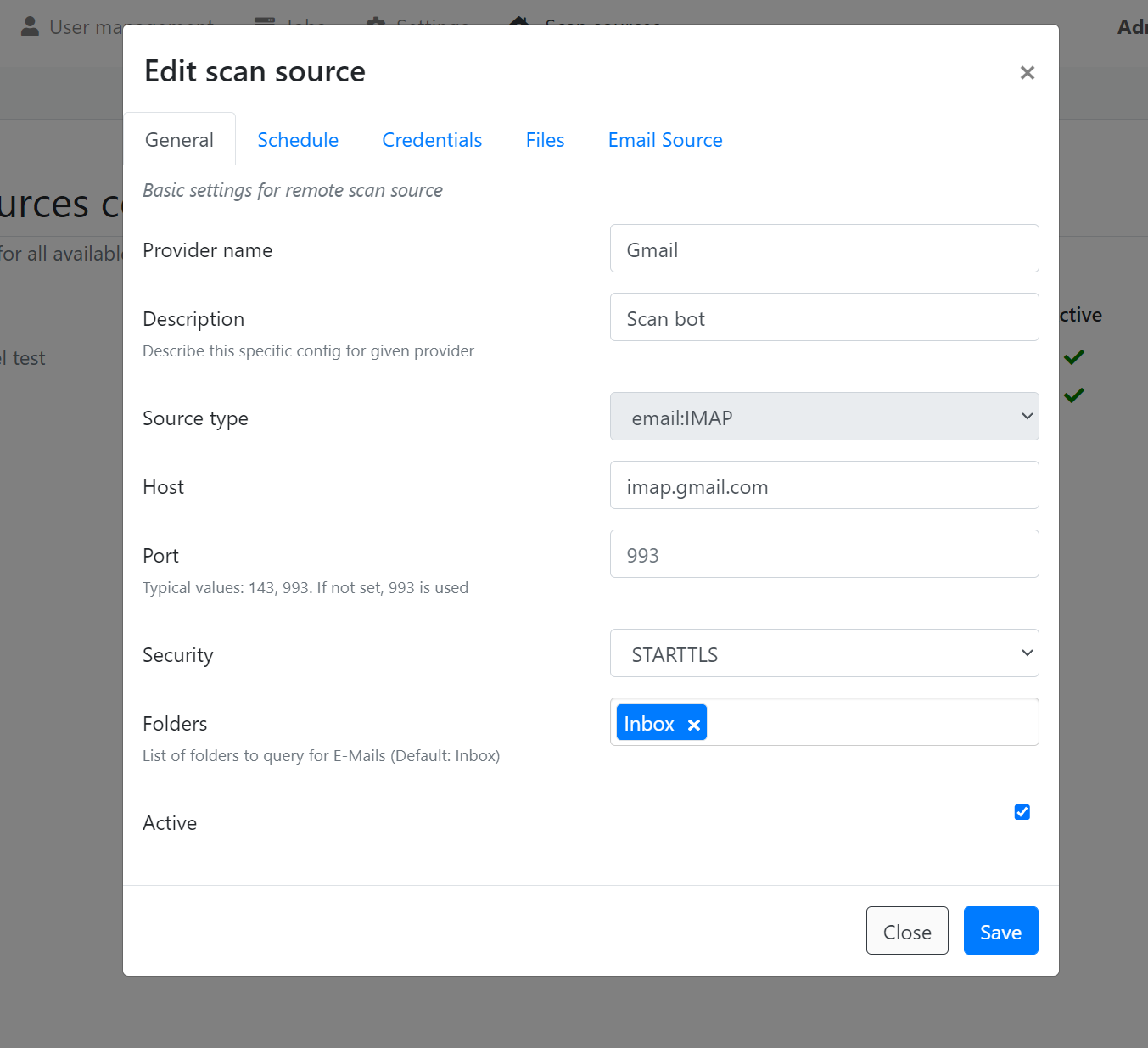
Another (new!) webservice feature is the "Scan sources" feature accessible from the top menu. In effect, it allows configuring a webservice to pull in files/URLs from a variety of sources. Currently, we support the configuration of IMAP accounts that are then regularly polled with a background (cron-like) job and ingested into the webservice. As this is still a work in progress, we will only show a few snippits:
However, setting up an E-Mail scan source is mostly self-explanatory and it's a fully working and implemented feature at this point, part of our next product release.
Other features that are often overlooked
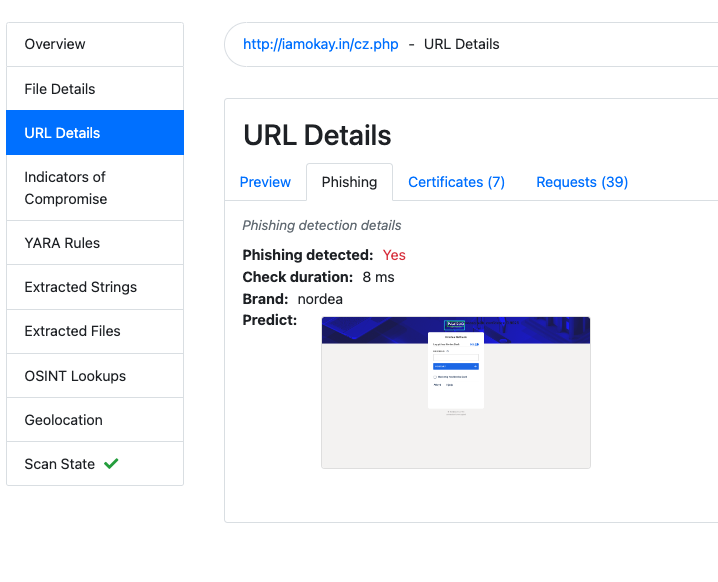
URL Phishing Detection
https://www.filescan.io/uploads/63c6f5a486e9647bb4c9c3dd/reports/2e496d50-da49-4633-a8a4-25f49252f8dc/url_details
OpenAPI / Python CLI
Certificate Whitelisting and Validation
Final Words
In this blogpost, a few key areas of the admin panel and backend features were showcased, outlining the maturity of the overall product and its flexibility in terms of ACL and customization.
Do you like what you see at www.filescan.io or in this blogpost and are interested in a live technical demo, data sheets and/or quote? Please get in touch with sales via our company contact form: https://www.filescan.com/contact/sales or E-Mail sales@filescan.io
Disclaimer: all screenshots were taken from a dev staging server populated with test data. Actual commercial product UX may differ slightly.









No comments:
Post a Comment